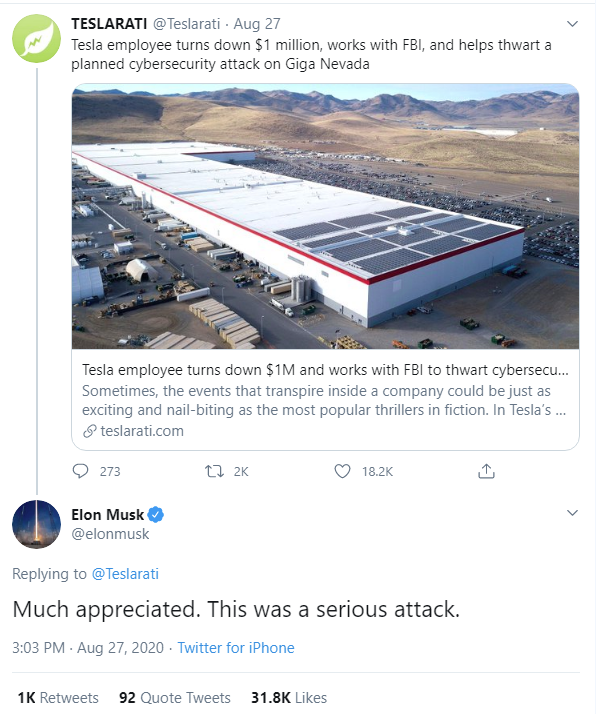
The US Department of Justice has pressed charges against a Russian who traveled to the US with the intent to recruit an employee of a Nevada company to install malware on their employer's network in exchange for about $1,000,000 USD.
It is speculated that this company is actually Tesla. They do have a factory in Sparks, Nevada.
As well Elon Musk did confirm that this was indeed a target against his company.

Egor Kriuchkov, a 27-year-old Russian. Is a member of a large criminal gang who planned to use malware to get access to the company's network. Which thereafter steal data, and then extort the company for a ransom.
In an attempt to make a diversion to cover the theft Kriuchkov made contact with the employee so that his crew will launch DDoS attacks to keep the company's security team distracted to give the employee time to plant the malware.
Kriuchkov and his crew never got to fulfill their goal as the employee decided to report this to the FBI.
The FBI intervened and kept Kriuchkov in their sights during his stay in the US, then eventually arrested the Russian national once they had gathered all the evidence, they needed to prosecute him in court.
Here's how everything went down.
On July 16th Kriuchkov contacted the employee via WhatsApp and tells him he plans to visit the US. They both knew each other since 2016. On the 28th Kriuchkov arrives in the states and travels to San Francisco then Reno.
August 1st - 3rd. Kriuchkov and the employee with friends travel to Lake Tahoe and Emerald Pools, Kriuchkov pays for all expenses. Throughout the day Kriuchkov tells the employee of the plans Initially, Kriuchkov told the employee he'd be paid only $500,000 for installing the malware. After this, the Employee alerted the FBI.
On the 7th of August Kriuchkov attempted to contact the employee again to convince them to partake in the scheme. Even saying if they have another employee in mind to "teach a lesson" which they can make it where that employee made the malware. The employee asks for $1,000,000 USD and $50,000 USD upfront.
Then on the 17th Kriuchkov reported to the employee that his crew had been planning to hit this building and even paid about $250,000 for this custom malware. The next day they had another meeting where Kriuchkov told the employee his crew refused to pay the upfront fee but agreed on the $1,000,000 payment. Which now the employee was told he needs to give any details on the company's network to help the malware. Then the next day on the 19th Kriuchkov said the gang eventually agreed to an upfront payment of 1 bitcoin.
August 21st, Kriuchkov told the employee he is leaving the country again and left instructions on how to contact him again. FBI alarmed made haste to grab him. The next day he was arrested in Los Angeles.
Kriuchkov was charged and could face up to five years in prison for his role in the scheme if found guilty.
If you would like a career in the cyber security field. Check out these cyber security degrees at UAT.






Comment