US authorities have charged three suspects that took part in a huge tech support scam campaign. With the help of FBI agents arresting one of their co-conspirators then used him as an informant. The Informant gave enough evidence with court documents detailing the whole scheme which gives a peek at the techniques and the inner workings of a tech support scam.
One of the suspects which was arrested pleaded guilty.
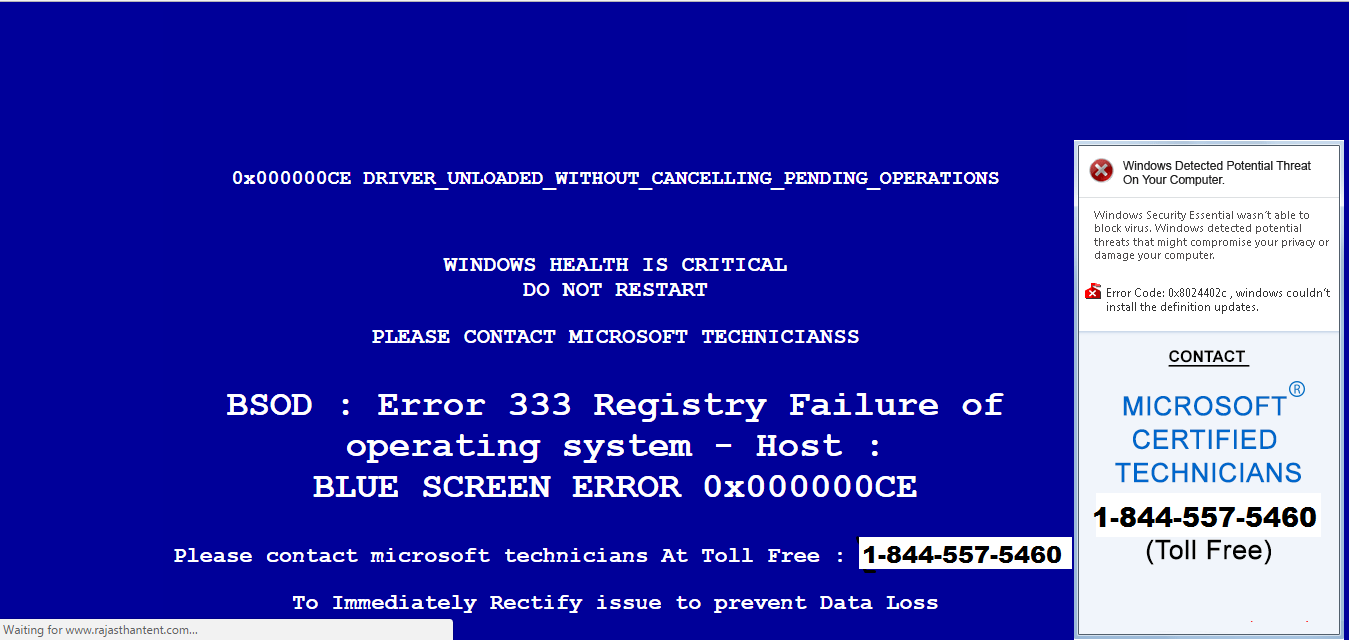
While actions were just now taken this has been an investigation since May 2019. The FBI arrested the Indian national on fraud charges. The informant agreed to cooperate with the FBI to seek leniency from US authorities in the case. He admitted to the authorities he was a member of the tech support scheme and he even gave up the names of three others who were involved in the scheme.
Two of the members owned actual call centers in India while the third lived in the US as was a "Money Mule" receiving money from the scammed victims into his US account then transferring the money to the Call Center Operators.
The informant's role was that he was a broker. He sold any of the "call traffic" and his role was the second stage of the whole tech support scheme. The first stage is the publishers, they are ones who make the tech support scheme with misleading errors and pop-ups that urge users to call a toll-free number.
They run ads on social media platforms and various websites for many different topics but as users clicked on the ads they are then redirected to the malicious sites. Some of these errors posed as Microsoft security alerts saying the machine was infected with malware.
Brokers operated as intermediaries between the publishers and the call centers. Brokers managed the telephony servers. Which they sold the "call traffic" to a call center operator willing to buy it. Some of the traffic was sold to other brokers, who had active call centers with free capacity.
The informant said that most of the transactions took place via WhatsApp and other online chat apps. How it would work is that Call center owners would get in touch with the brokers, agree to a price per unit of calls, then provide a number to which the broker could re-route calls from tech support scam victims.
The Victims were all elderly citizens who lacked technical skills to determine that the security alert was a fraud.
The worst part is how some call operators were able to convince some of the victims to allow remote access on their computers and download the software for them all in hopes of "fixing" their issue.
Any money received as payments, or surreptitiously stolen from victims' bank accounts, would then be transferred to the Money Mule.
The Court documents list only a few of the victims who lost money as part of these scams with a total estimated loss of around ~ $10,000s USD. But the FBI determined this tech support operation has been ongoing since 2017 and believe there is a lot more money that has been lost.
While the Call Center operators are at large in India. A money mule was arrested earlier this year and is facing charges up to 20 years in prison.






Comment