Last week the UAT CCDC team competed in the last invitational—or practice round—of the season for the Western Regional Collegiate Cyber Defense Competition (WRCCDC). At WRCCDC colleges compete against each other in maintaining and securing servers. This experience was only our second invitational. (You can learn more about our first go around here.)
.png)
WRCCDC provides real-world experience in a fun, team environment. While we travel for competitions, we complete the invitational rounds in the UAT Cyber Warfare Range (AKA "The Cave") right here on campus.
Each team is given a network and has to defend it from attackers, who are professional red teamers. There are different methods of scoring surrounding services, injects and exploits. Each of portion plays an important role in successful completion of the competition and real life cybersecurity scenarios.
The service score is the most straightforward of the scoring methods in which a server is tested for the service it is providing. For example, a computer that is hosting an online store will be tested to see if that store is accessible to the customers. Our strength in keeping services up is having a variety of knowledge of how to use all kinds of services. This aspect of the invitational went okay as we placed in the top eight in services. Everyone on the team is motivated to improve on service checks by training before the qualifier.
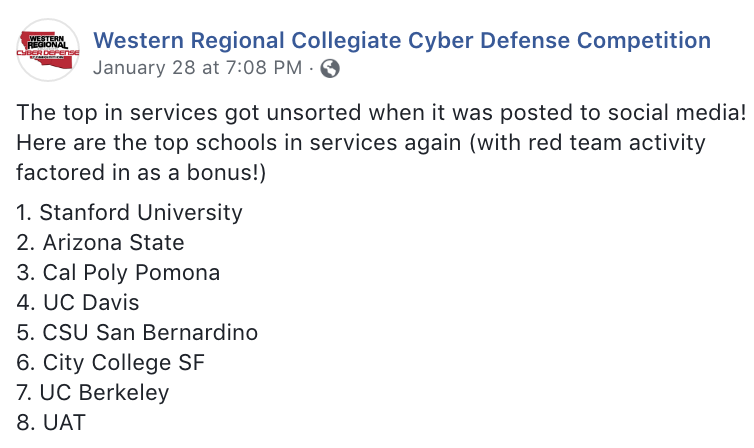
Another important element of scoring is injects. An inject is a task that you are given and have to complete within a set time. We have not received the inject scores for the last invitational, but we learned a lot. Our team works well under pressure, which made it easier to get injects turned in. I think this year's team has a good balance between injects and services.
Exploit is the last type of scoring and encompasses how well you can defend against the red team. A red team is a group of people that will try to use exploits to gain unauthorized access to your system. Keeping them out is important because it can add chaos to an already chaotic environment.

While we did not get first in this invitational like we did last time, we learned a lot through trial and error. We have already developed strategies to prevent or mitigate what went wrong this time, so we can do better in the qualifier. An important part of learning network security is the ability to self analyze and improve from mistakes. The industry is always evolving; one method of security that works may not work in a few weeks. Being adaptable is a quality that our current team has, and I think that will help us in the qualifier.
Want to join us? We're always looking for passionate people to join the team or practice squad. You can learn more here.





Comment